
Despite the fact that secure email technology has existed for decades, email continues to be a source of constant breach. Creative integration of secure cloud storage technology presents a viable alternative to making email secure without making it unusable.
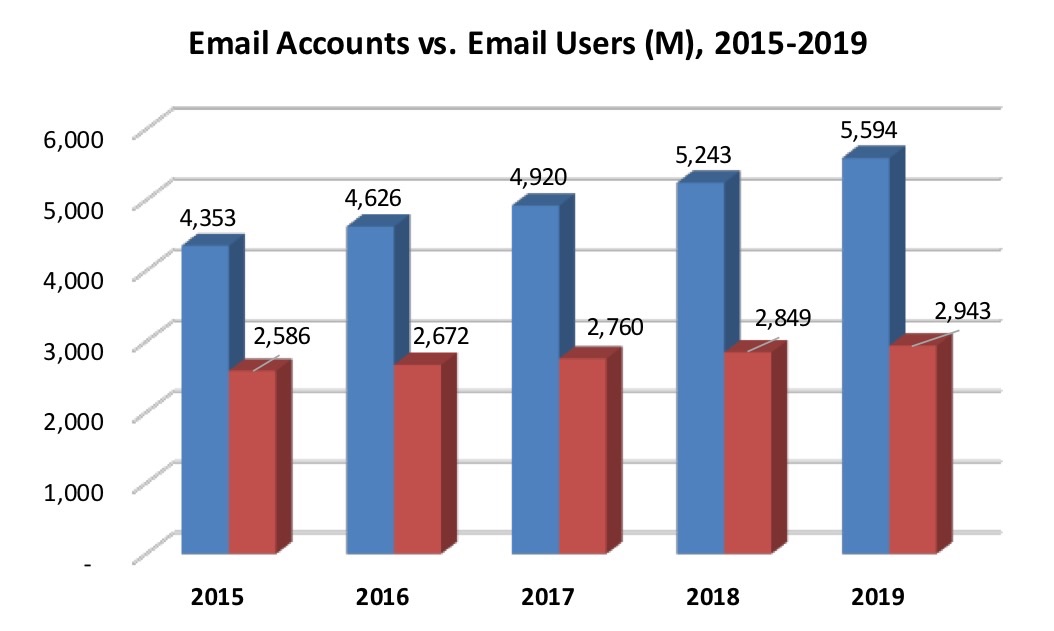
Ashley Madison, US Department of State, Sony Corporation and Hillary Clinton all have something in common, namely, all are high profile examples of email and its lack of security. Email is inherently not secure by design. Back in the 1960s, when it was first developed the need for security was not a requirement on a nascent Internet used by a handful of researches that essentially new each other. Fast forward 50 years and some 5.5 billion email accounts later (Radicati, “Email Statistics Report, 2015-2019”) email has since become the primary communication medium on the Internet and its vulnerability a consistent source of pain for organizations and individuals the world over.
Attempts to add security to email have been made but judging by the near daily news of email related security breaches, these solution have not taken hold. Technologies like PGP and S/MIME are truly secure methods for protecting email. But despite their existence for many decades, most people have never seen a PGP or S/MIME email, much less sent one.
So why, when there is clearly a need for email security, are long existing solutions not used? One commonly cited reason is that these solutions require either additional knowledge or software on both ends of the communication. According to a recent Forbes article, when Edward Snowden asked a reporter to use an end-to-end encrypted email to share details of the NSA surveillance program the reporter couldn’t get the system to work. Given the limited uptake of these secure alternatives, the assumption that a recipient is prepared to receive your encrypted message has proven highly unlikely.
What the lack of secure email usage reveals is that email security can not depend on end users learning new technologies or adopting new workflows. If email is to be secure, the security needs to be provided in a way that is completely transparent to the end user. In other words, no training or software should be required. An effective solution to email security will have to meet the end user on his terms and not the other way around. The implication is that email security can not rely on email since it is inherently not secure and any attempt to make it so, unless widely and rapidly adopted, will render it useless as a communication medium - the cure kills the patient.
"What the lack of secure email usage reveals is that email security can not depend on end users learning new technologies or adopting new workflows."
One strategy to make email secure without breaking it as a means of communication is to seamlessly introduce secure technologies in a way that is not disruptive to the email experience. MxHero’s Mail2Cloud technology is a prime example of this approach. Mail2Cloud Fusion automatically moves unsecure email attachments to secure cloud storage and replaces them with secure cloud storage links. Links can require recipient authentication, be set to expire in 7 days, configured for "view-only" with no download, etc. The process is configured by the administrator and is completely transparent to the sender as the transformation occurs after the email has been sent. For the end user there is no need to install additional software or attach files to email in some new way. With Mail2Cloud Fusion, it is email as usual.
MxHero’s Mail2Cloud augments email security by leveraging non-email technology but with a significant effort on not breaking the email experience. MxHero is not alone in its acquiescence that the solution to email security exists outside of email. Nearly every cloud storage provider offers an Outlook plugin to send attachments as secure links. Banks and other regulated organizations have long used secure portals that only use email as a means to send authenticated links to a secure visualization of messages. Mail2Cloud’s core difference is the design goal that the integration of secure technology be as transparent possible - meaning there is nothing for the end user to see.
Mail2Cloud’s transparency and central administration makes it a potent security solution from the perspective of the organization. By not having end user (client-side) components, Mail2Cloud security does not depend on end-users remembering to use it. Nor does the security depend on client-side software to be installed on users' many devices. Simply put, Mail2Cloud Fusion is always on - always moving files from unsafe email to secure cloud storage. Existing solutions that rely on user vigilance with regards to utilization are highly prone to human error and therefore constantly exposed to critical security breaches. Another way to put it, a seat belt is a great safety device if you remember to use it.
Despite its shortcoming, email continues to outlive its oft announced demise. In a recent study by the Radicati group, email continues to grow. It is a communication medium without parallel, in part because it is so open. But it is this openness that makes it an inappropriate tool for secure communication. Born in a different age, email has been unable to adapt to a world in which so much information can be so easily exploited from anywhere on the globe. But there are ways in which email can leverage other technologies to overcome its shortcomings and adapt while preserving the powerful simplicity and ubiquity that is at the essence of its abiding charm.